Get a better Intune policy report part 3. (FINAL)
By combining information from MDMDiagReport.xml and system registry
What was my motivation to create my own rsop-like or gpresult-like Intune policy report? I was super frustrated by the built-in one (that you can generate in System settings) because it misses a lot of information plus shows a lot of useless ones.
In my previous post, I've talked about parsing Intune MDMDiagReport.xml report and how to extract a lot of helpful information from it.
As was stated MDMDiagReport.xml doesn't contain all Intune policies processing data. Scripts, Remediation scripts, and Win32Apps are missing. Therefore this final post will be about merging data retrieved from MDMDiagReport.xml with data from the client's system registry which contains needed information to get a complete picture.
Result will be PowerShell function (Get-ClientIntunePolicyResult) (now part of the IntuneStuff module) that outputs PowerShell object or HTML report about every Intune policy, script, application etc applied to your computer.
TL;DR
- Install module IntuneStuff
- Import the module
- Run PowerShell function
Get-ClientIntunePolicyResult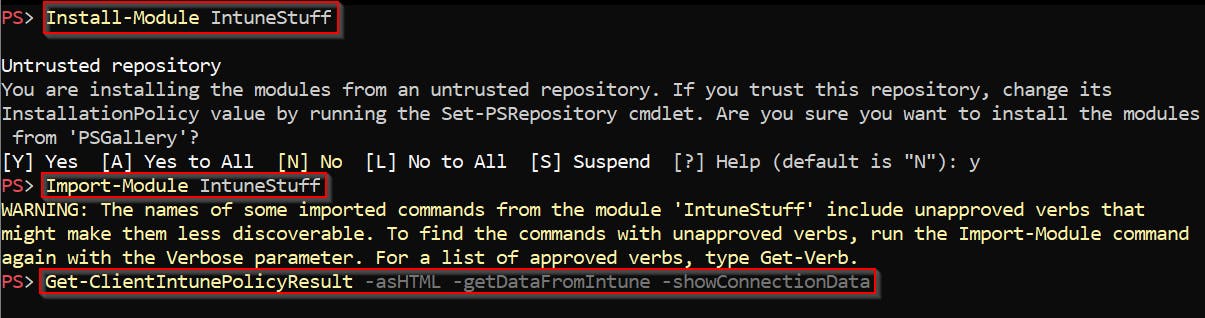
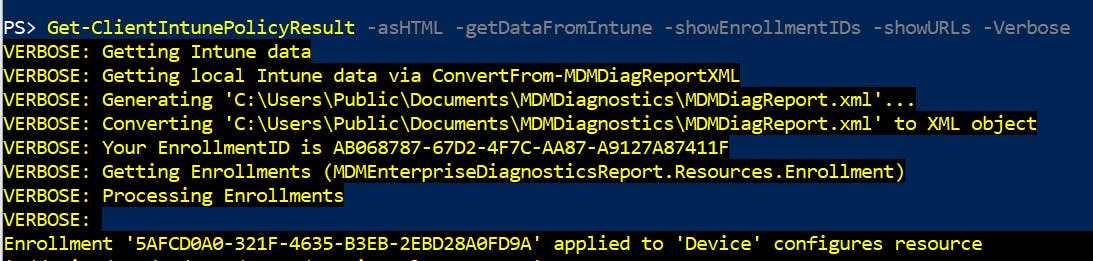
To get most detailed report (as HTML) call it like:
Get-ClientIntunePolicyResult -asHTML -getDataFromIntune -showConnectionData -showEnrollmentIDs -showURLsand get result (interesting parts are highlighted) similar to
TIP: To get a working HTML report, open it in Chrome browser, not Internet Explorer!
Why should I care?
Built-in Intune HTML report has several disadvantages:
- it is very confusing
- is super long
- shows a lot of useless information (I am looking at you KNOBS)
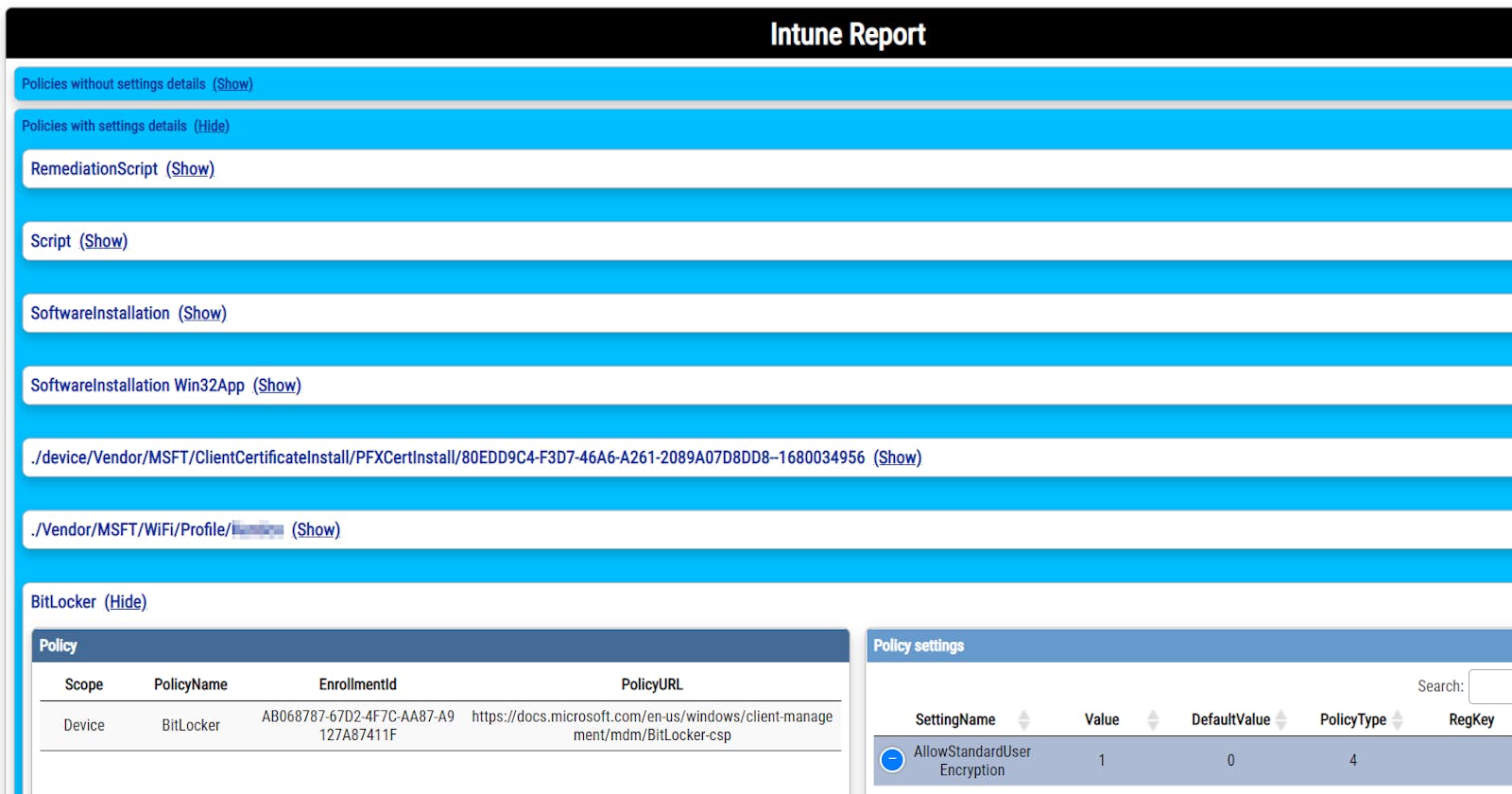
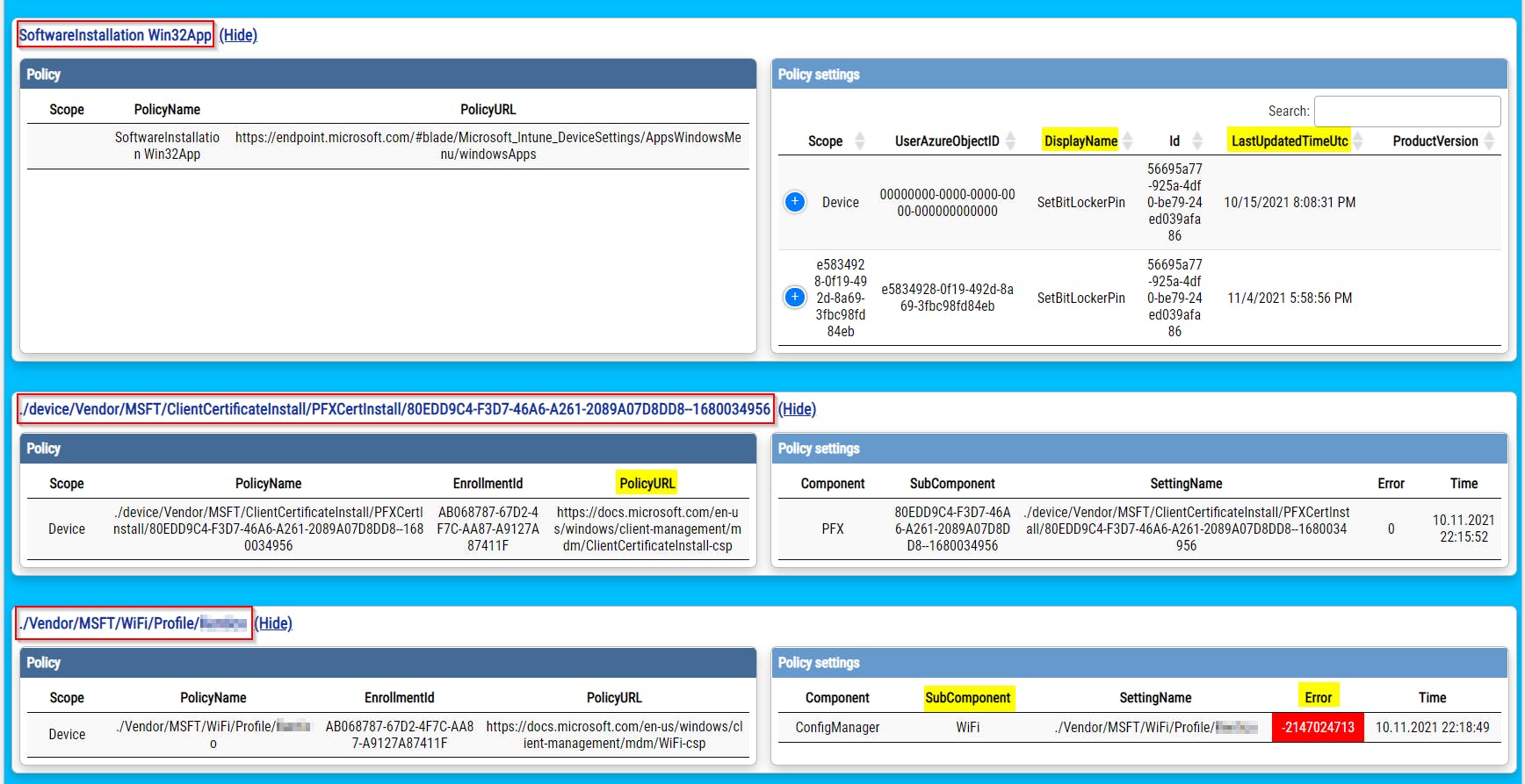
- doesn't group information into meaningful sections (Bitlocker, Defender, MSI installations,...)
- important data are missing
- doesn't show Scripts, Win32Apps, and Remediation scripts at all
- doesn't show details like what has policy changed (registry key/value), when was the last time policy was applied, errors
- shows IDs instead of policy names
- shows user01 instead of user SID
- ...
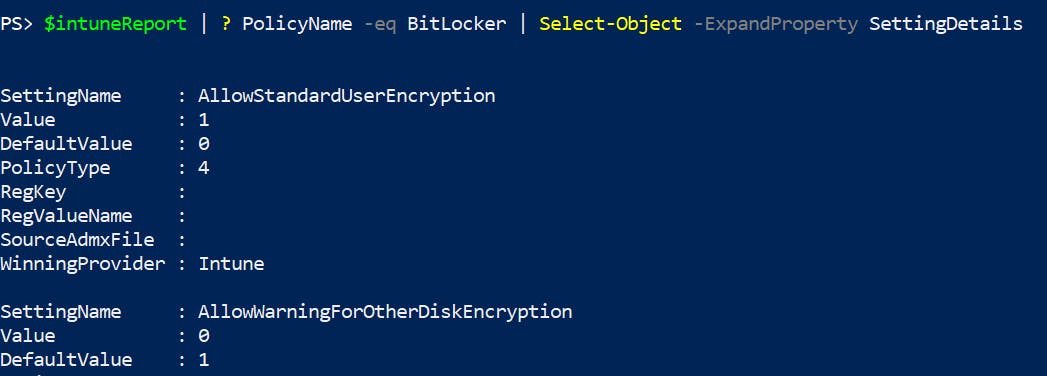
One example for all: searching for Bitlocker settings
Built-in Intune report 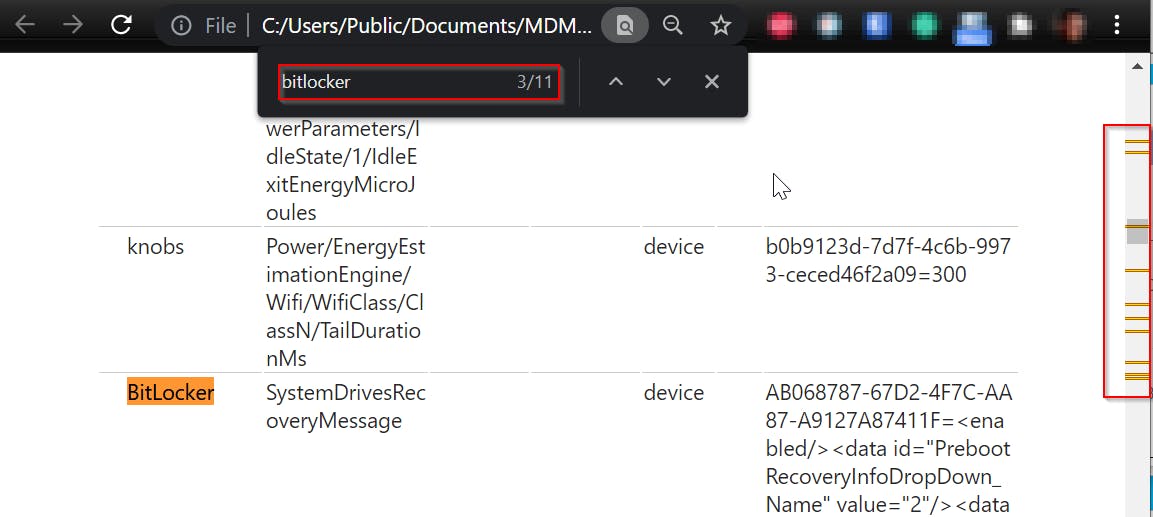
My report 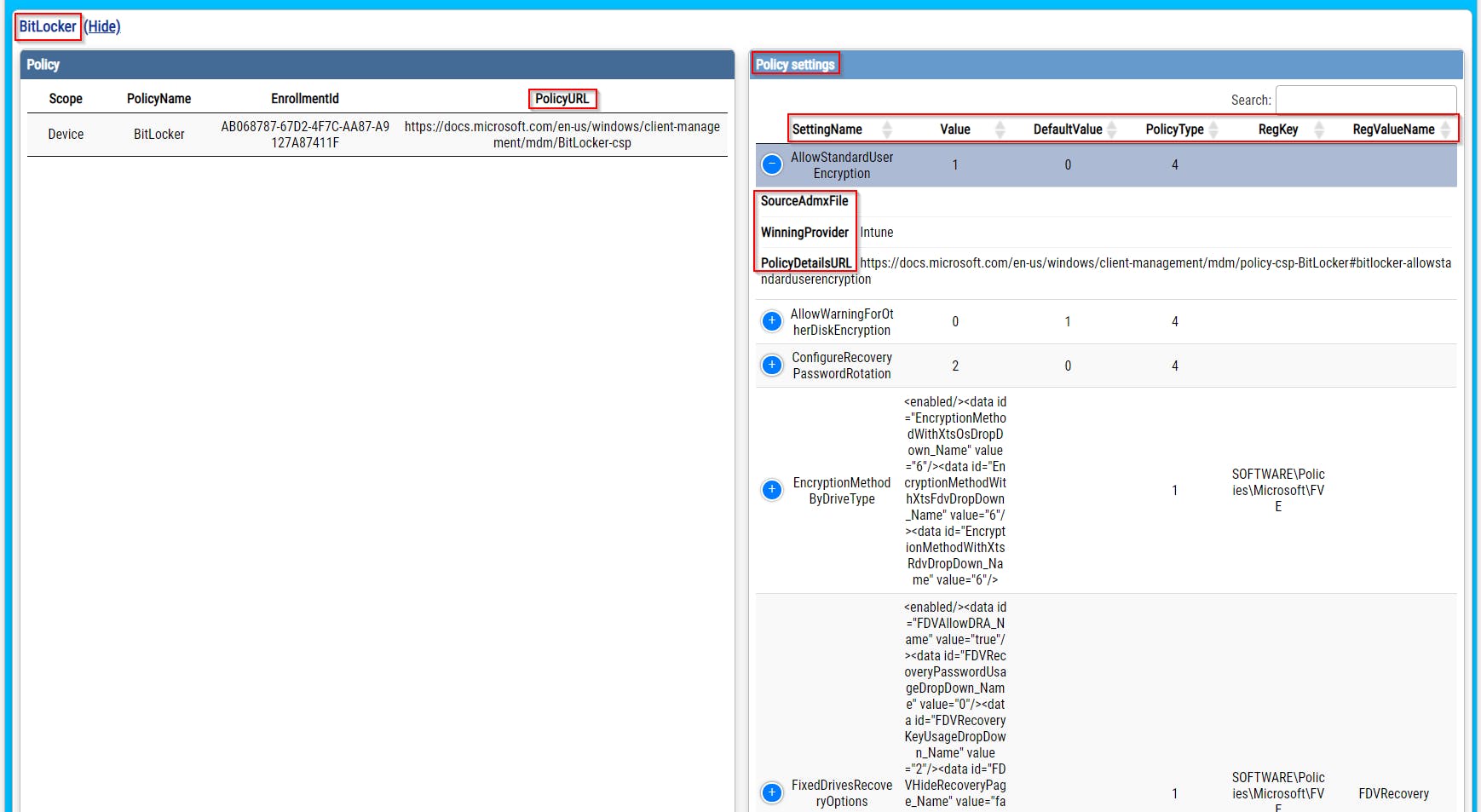
What irritate me most is that all necessary data are stored on the client, so why isn't Microsoft using them to generate usable report? It was possible for old school
GPO, so why not for 'modern' Intune?
What else interesting data do I get?
- PolicyURL = URL to policy documentation (if available)
- IntuneWin32AppURL, IntuneScriptURL, ... = URL of such item in Intune portal
- and lot more, please check screenshots bellow
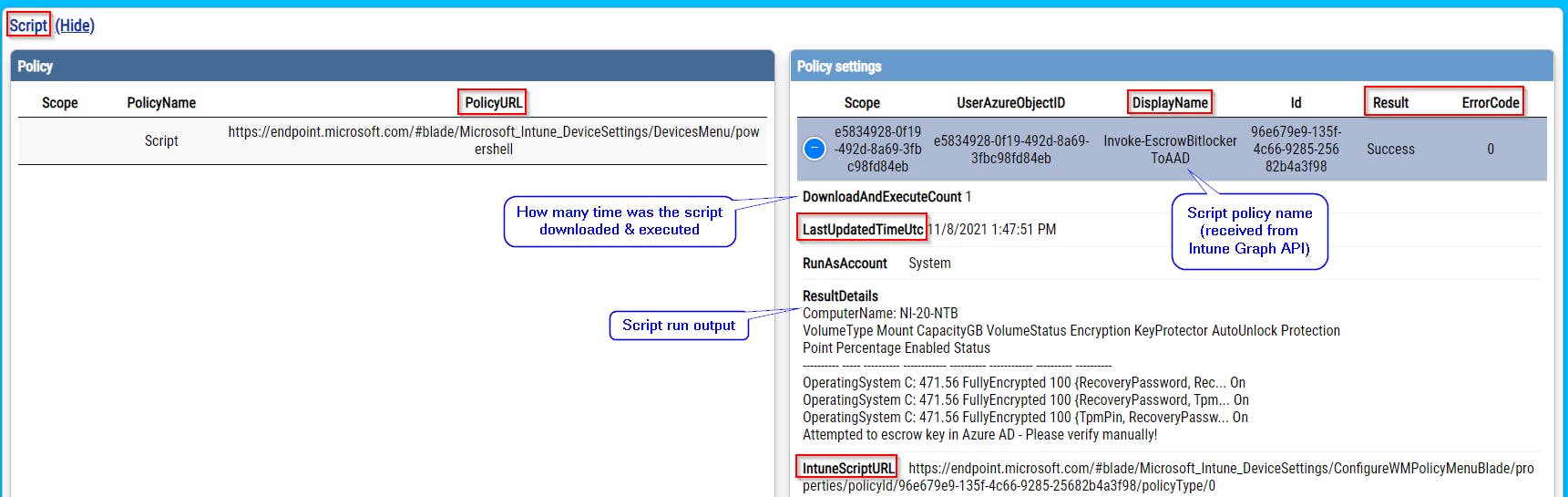
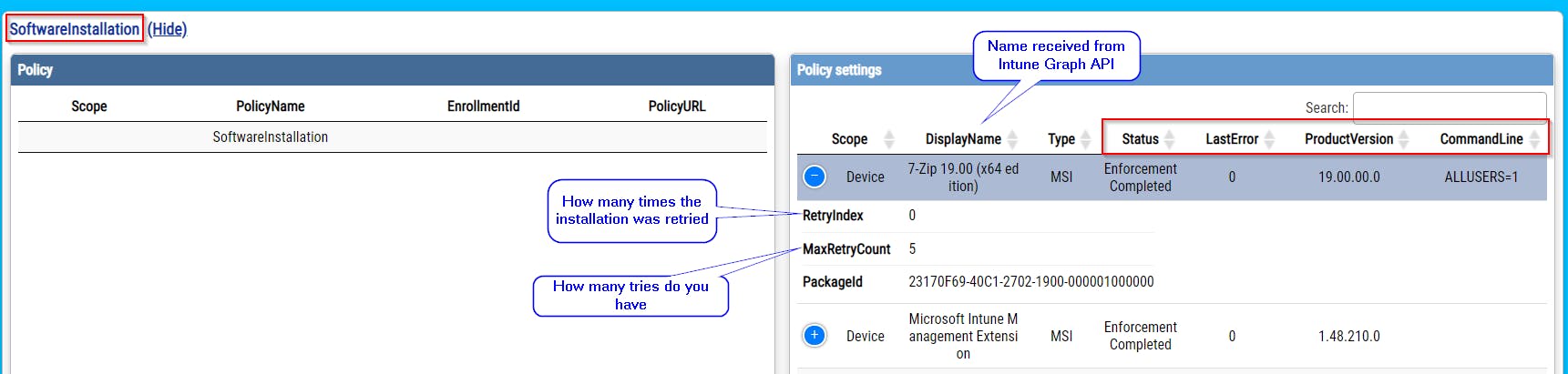
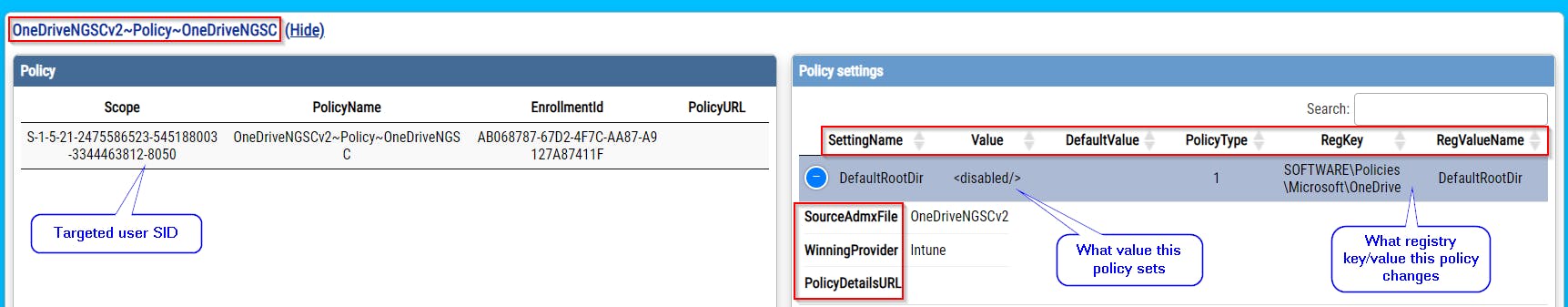
Where can I get processing data for Scripts, Remediation scripts, and Win32Apps?
Intune client stores a lot of useful information in the system registry. In general, it is at HKLM:\SOFTWARE\Microsoft\IntuneManagementExtension.
Win32App data
Win32App data are stored at HKLM:\SOFTWARE\Microsoft\IntuneManagementExtension\Win32Apps
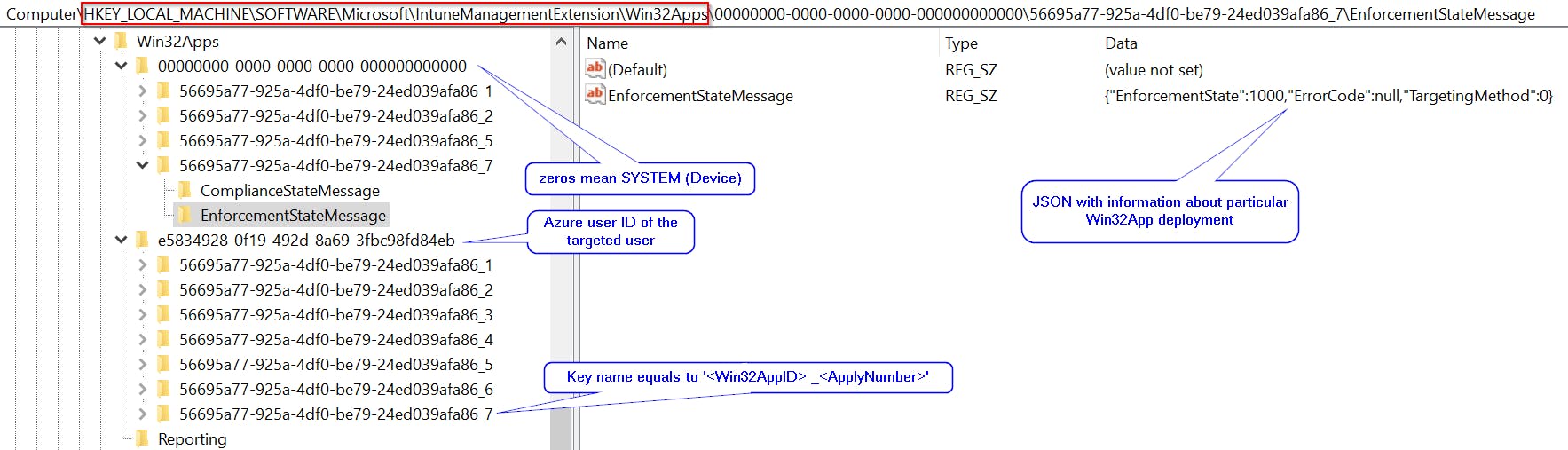
Scripts data
Script data are stored at HKLM:\SOFTWARE\Microsoft\IntuneManagementExtension\Policies
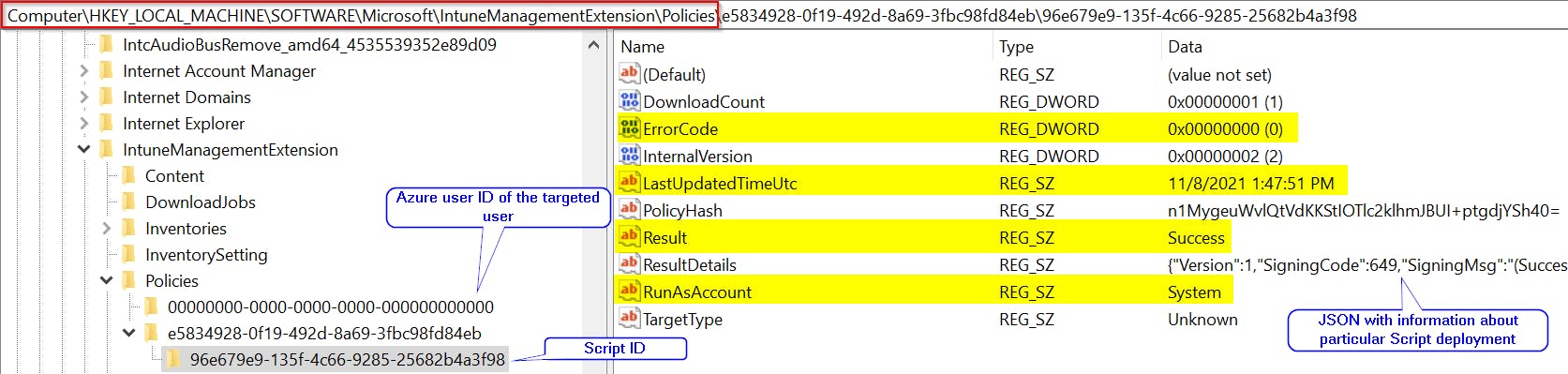
Remediation scripts data
Remediation scripts data are stored at HKLM:\SOFTWARE\Microsoft\IntuneManagementExtension\SideCarPolicies\Scripts
Executionkey contains last execution timeReportskey contains last run result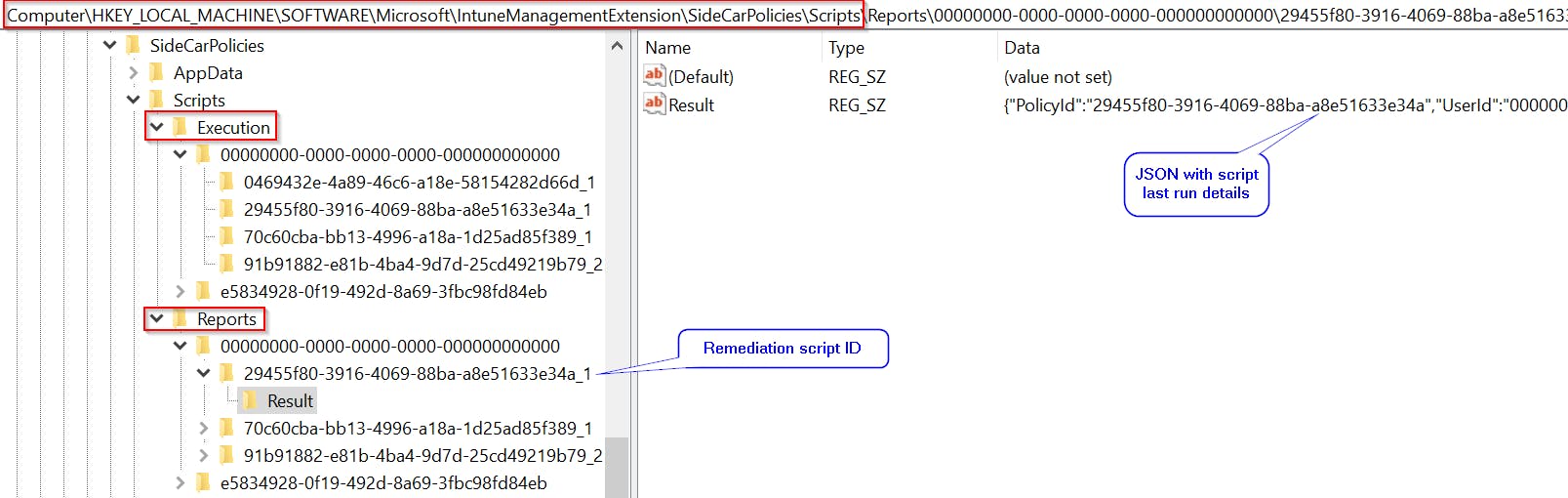 Converted
Converted ResultJSON can look like this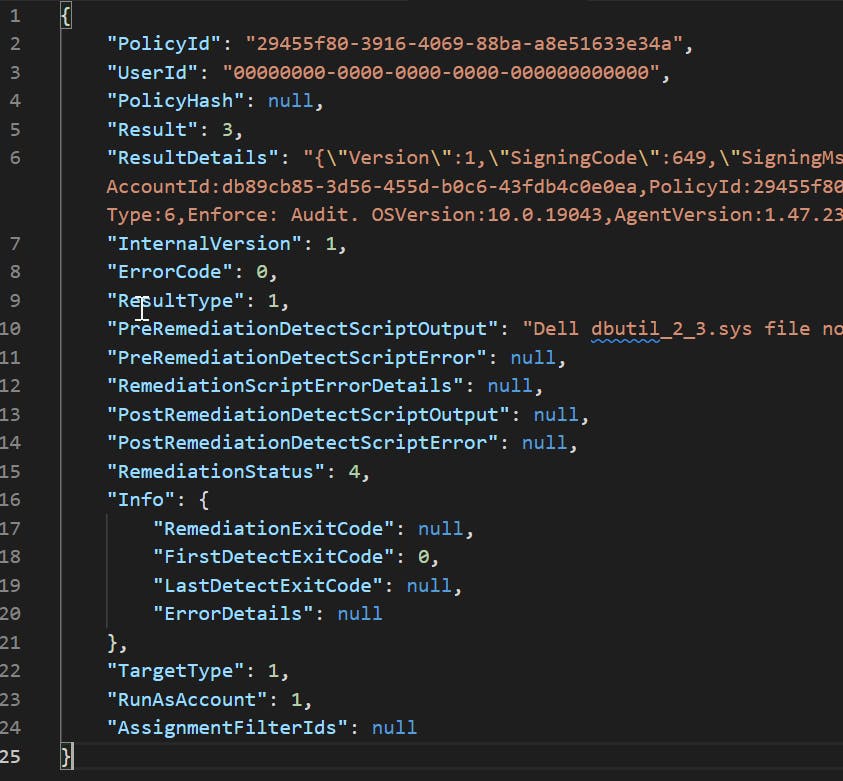
Where can I get Intune policies names?
As far as I know, Intune doesn't store policies name (like you can see them in Intune admin web portal) locally. If you are lucky, you will get a policy ID that you have to translate to the corresponding Intune policy name. To do that you have use Intune Graph API.
For working with Intune Graph API I am using the official PowerShell module Microsoft.Graph.Intune.
- For making connection
Connect-MSGraph. - For data retrieval
Invoke-MSGraphRequest
$intuneRemediationScript = Invoke-MSGraphRequest -Url "https://graph.microsoft.com/beta/deviceManagement/deviceHealthScripts" | Get-MSGraphAllPages
$intuneScript = Invoke-MSGraphRequest -Url "https://graph.microsoft.com/beta/deviceManagement/deviceManagementScripts" | Get-MSGraphAllPages
$intuneApp = Invoke-MSGraphRequest -Url "https://graph.microsoft.com/beta/deviceAppManagement/mobileApps" | Get-MSGraphAllPages
It seems to me that a lot of Intune policy types cannot be linked to locally applied policies. At least I wasn't able to find their IDs in MDMDiagReport.xml. That's the reason that just some of the policies get a translation.
How can I use function Get-ClientIntunePolicyResult
As was already stated function Get-ClientIntunePolicyResult can outputs HTML or PowerShell object.
Getting object:
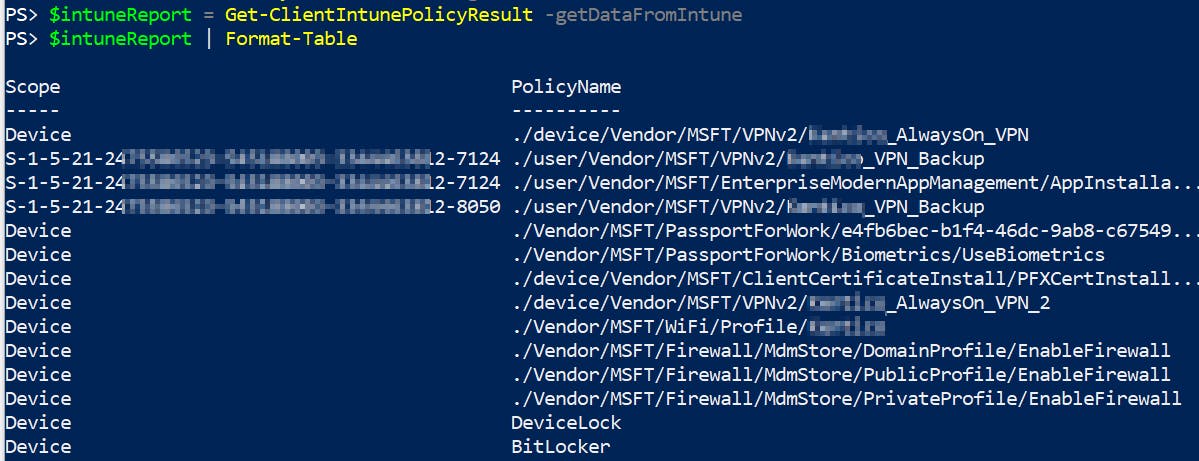
 Getting HTML report:
Getting HTML report:
Summary
There are still things to improve. Like getting error details from event log or local log files or making the function Get-ClientIntunePolicyResult faster. But in general, the work is done. We now have a useful 'gpresult' like tool for Intune policies 👍