If you are an Azure administrator you are probably aware that it can be pretty dangerous to let users give permissions consent to any Azure application that is in the wild. Because it can lead to illicit consent grant attack which seems to be more and more popular among the hackers.
One of the solutions to this problem is to require admin consent. If you enable this feature, whenever a user wants to grant consent to not yet allowed application, admins will be notified to allow/deny such request via email.
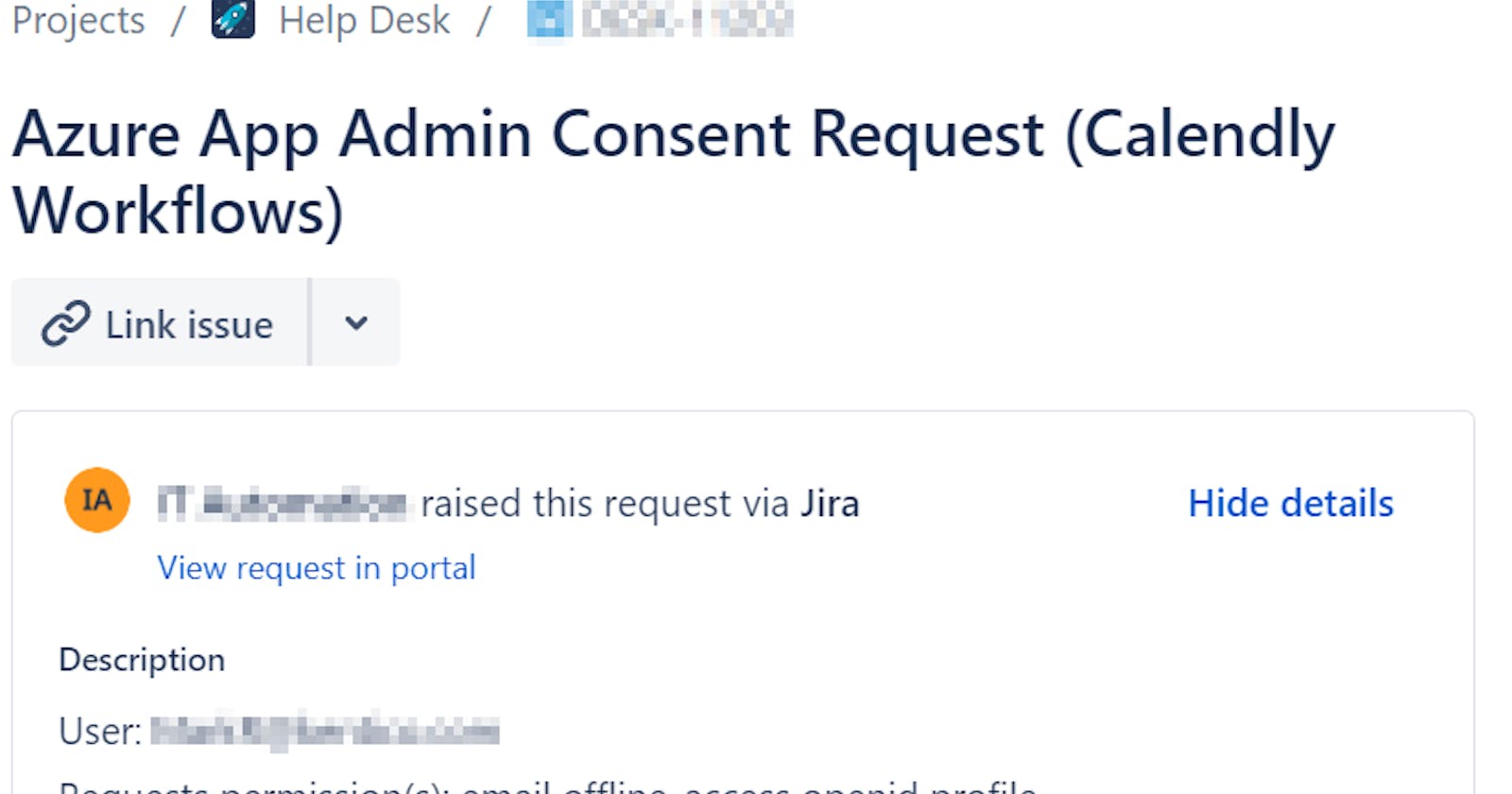
This is OK, but if you are using JIRA as your support ticket solution, wouldn't it be nice to also automatically create Jira ticket? 😉
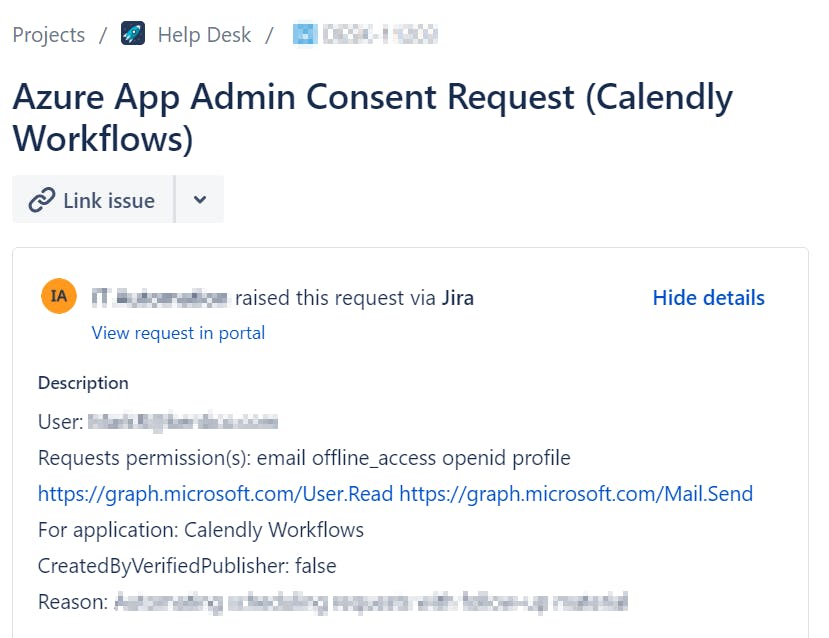
Such Jira ticket can contain information like:
- the name of the application
- requested permissions
- who requested the consent
- whether it is created by a verified publisher
- the reason why the user wants to use this application
- etc
And the result can look like 👇
Prerequisites
- Account with permissions to create Jira ticket + its API token
- Azure Service principal (Enterprise Application) with permissions to read Azure admin consent requests and Azure application information (to get publisher information)
- My AzureADStuff module
- A scheduled task that will run periodically PowerShell script that will check for new admin consent request and if so, create Jira ticket
How to create a Jira ticket isn't part of this article, but can be found at how-to-create-a-jira-ticket-using-powershell.
Prepare service principal (Azure Application) for making Graph API calls
To be able to work with Azure non-interactively, we need to create a service principal account that will be used in our PowerShell script to gather all data we need.
- Log in to the Azure portal
- Create a new App Registration (
IT_Azure_Consent_Readin my case)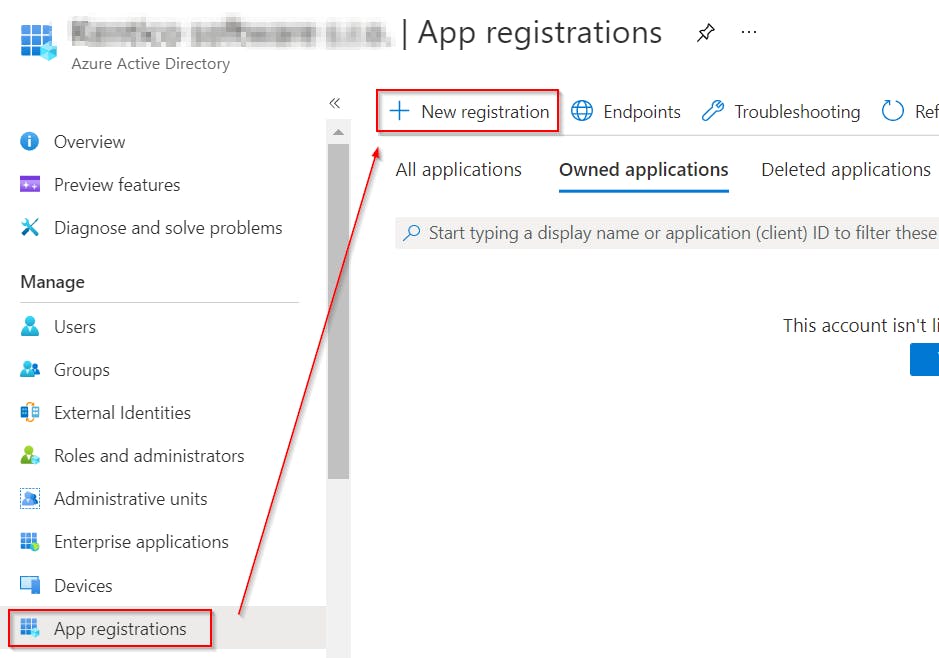
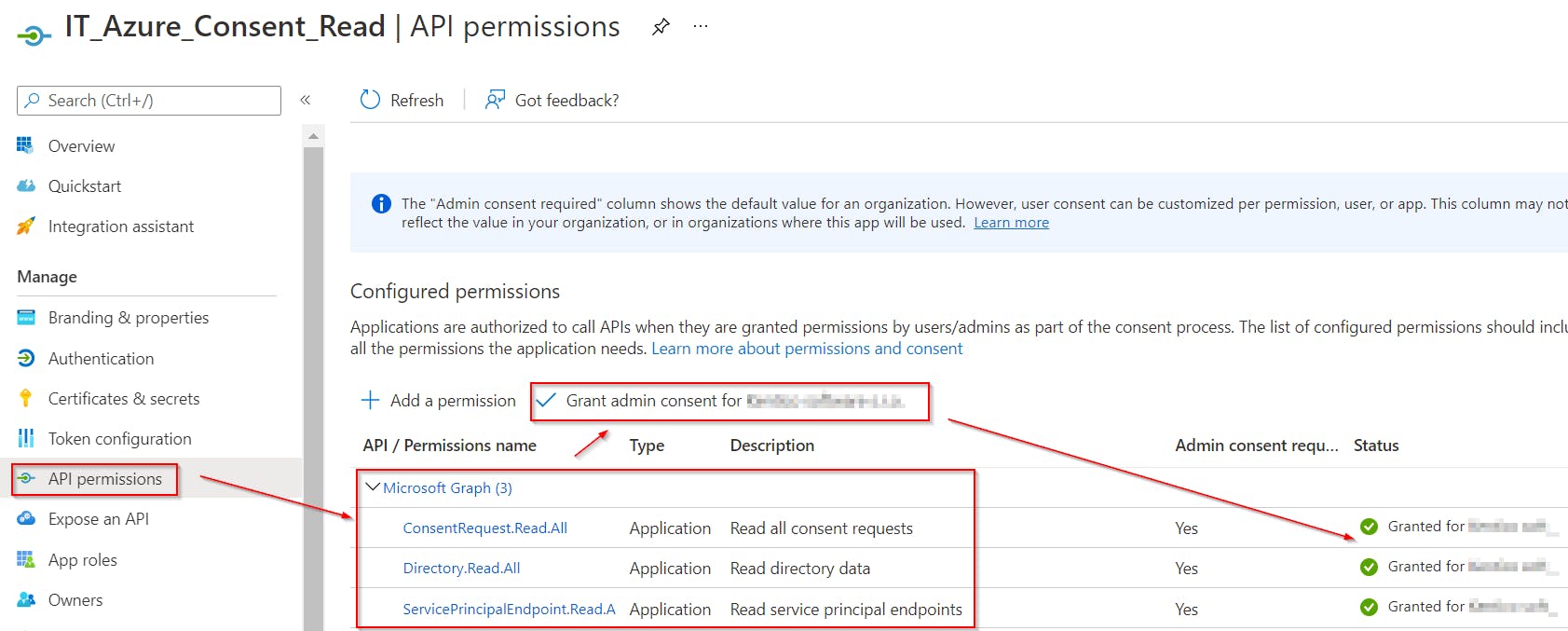
- Grant application following application Graph API permissions:
- ConsentRequest.Read.All
- Directory.Read.All
- ServicePrincipalEndpoint.Read.All
- Don't forget to grant admin consent too!
- Create application secret or certificate so we can authenticate as this application
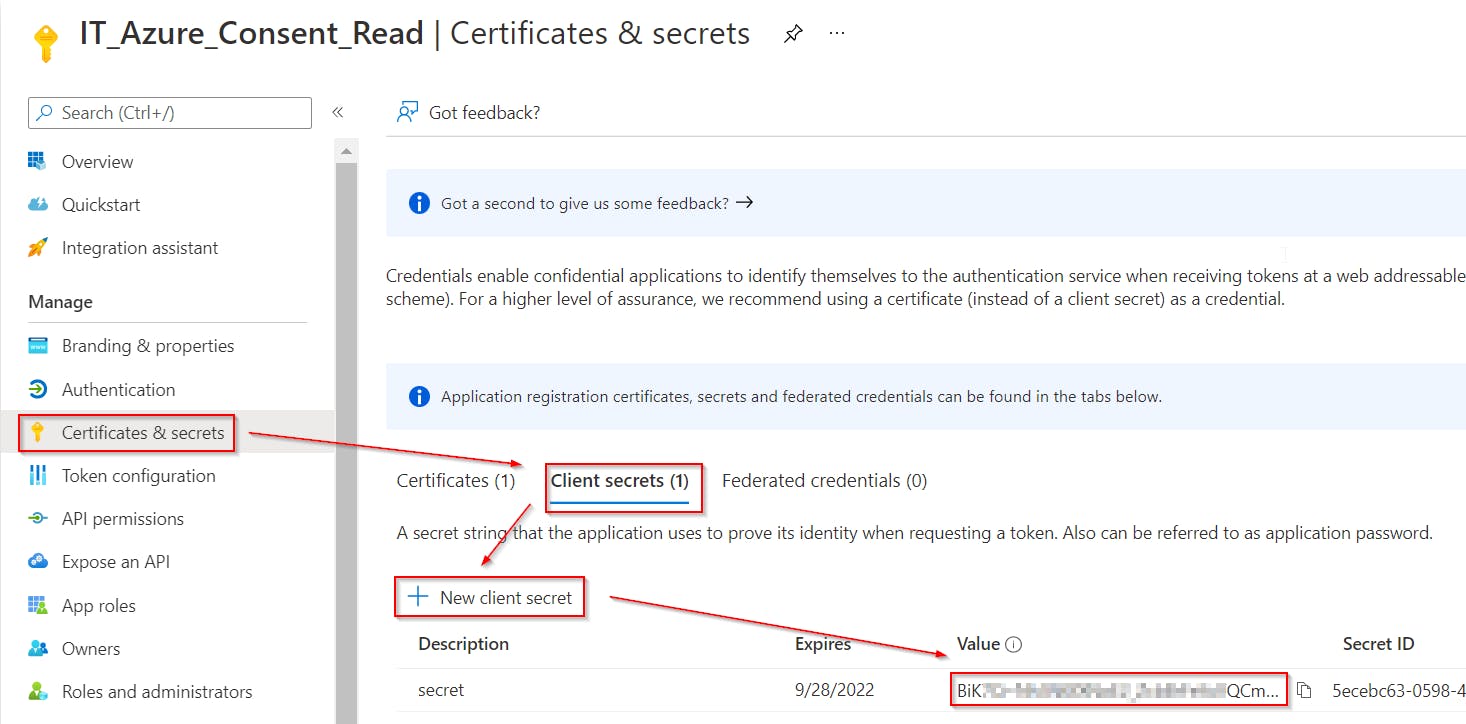 Store this secret password at the safe place for later use!
Store this secret password at the safe place for later use!If you want to use certificate to authentication, you can use function
Add-AzureADAppCertificatewhich is part of the AzureADStuff module. It can be used likeAdd-AzureADAppCertificate -appObjectId <IT_Azure_Consent_ReadAppObjectId> -password (Read-Host -AsSecureString)
Getting admin consent requests
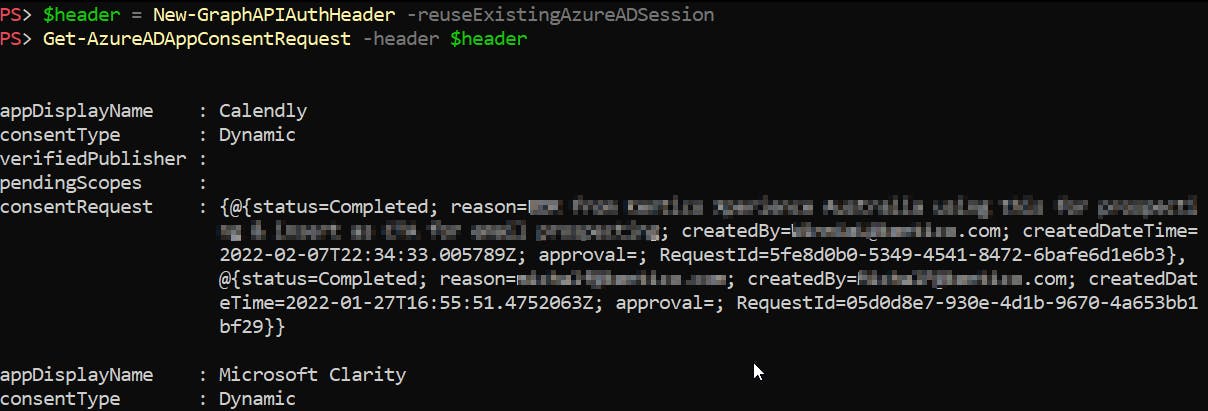
To get all admin consent requests use Get-AzureADAppConsentRequest PowerShell function 😉 which is part of my module AzureADStuff.
The function uses these URLs to get the required data:
https://graph.microsoft.com/beta/identityGovernance/appConsent/appConsentRequestsfor reading admin consent requestshttps://graph.microsoft.com/beta/servicePrincipals?$select=appId,verifiedPublisherfor reading application publisher data
The result of the Get-AzureADAppConsentRequest can look like this 👇
Put it all together
To summarize it a little bit, we have:
- Azure application (
IT_Azure_Consent_Read) with appropriate permissions to get admin consent requests from the Azure and know its secret, to be able to authenticate and Get-AzureADAppConsentRequestfunction to actually get the admin consent requests data.
Now we need to put it together and create a PowerShell script that
- will be run on schedule (using Task Scheduler),
- check new admin requests and if find some, creates Jira tickets for every one of them,
- saves processed requests in the XML file (to be able to track the changes),
- closes Jira tickets for solved requests + adds comment about who accepted/rejected the request
And the result can look like this AzureAD_admin_consent_requests_Jira_ticket_creation.ps1
AzureAD_admin_consent_requests_Jira_ticket_creation.ps1script is just a template. To make it work, you have to check and fix lines that starts withFIXME. Therefore export Jira and Azure app credentials, defined App Id etc.
Feel free to write comment in case of any problems. 👍